Secure Your Azure Functions: Use Managed Identity for AzureWebJobsStorage
When using an Azure Function app, it is necessary to connect it to a storage account, often referred to as Host storage. This storage is utilized by the Functions runtime, as well as by various triggers and bindings to coordinate between multiple running instances. It is also used for host logs and managing state, among other purposes. The Azure Function app establishes a connection to this storage account through the AzureWebJobsStorage configuration. By default, AzureWebJobsStorage is configured with a connection string to the storage account that uses an account key. However, this approach poses a security risk, as it requires careful management of key storage, key rotation, and other security considerations.
As a best practice, it is recommended to use Azure Managed Identity (often referred to as MSI) whenever possible when connecting to storage accounts and other Azure services. With managed identity, Azure automatically manages secure access to Azure resources without the need for providing explicit credentials in code or configuration.
This article guides you through the process of using managed identity for AzureWebJobsStorage. At a high level, the following steps are required:
Enable system-assigned managed identity for the function app.
Grant the function's identity access to the storage account.
Edit the
AzureWebJobsStorageconfiguration.
Enable system-assigned managed identity for the function app
In the Azure portal, navigate to the Azure Function app.
Select the Identity option from the menu blade.
On the System assigned tab, set the status to "On" and Save it.

Grant the function's identity access to the storage account
Create a role assignment granting the system-assigned identity access to the storage account.
Navigate to the storage account that was created with the function app.
Select Access Control (IAM). You can view and configure who has access to the resources from IAM.
Click Add and select Add Role Assignment.
Search for the 'Storage Blob Data Owner' role, select it, and click Next.
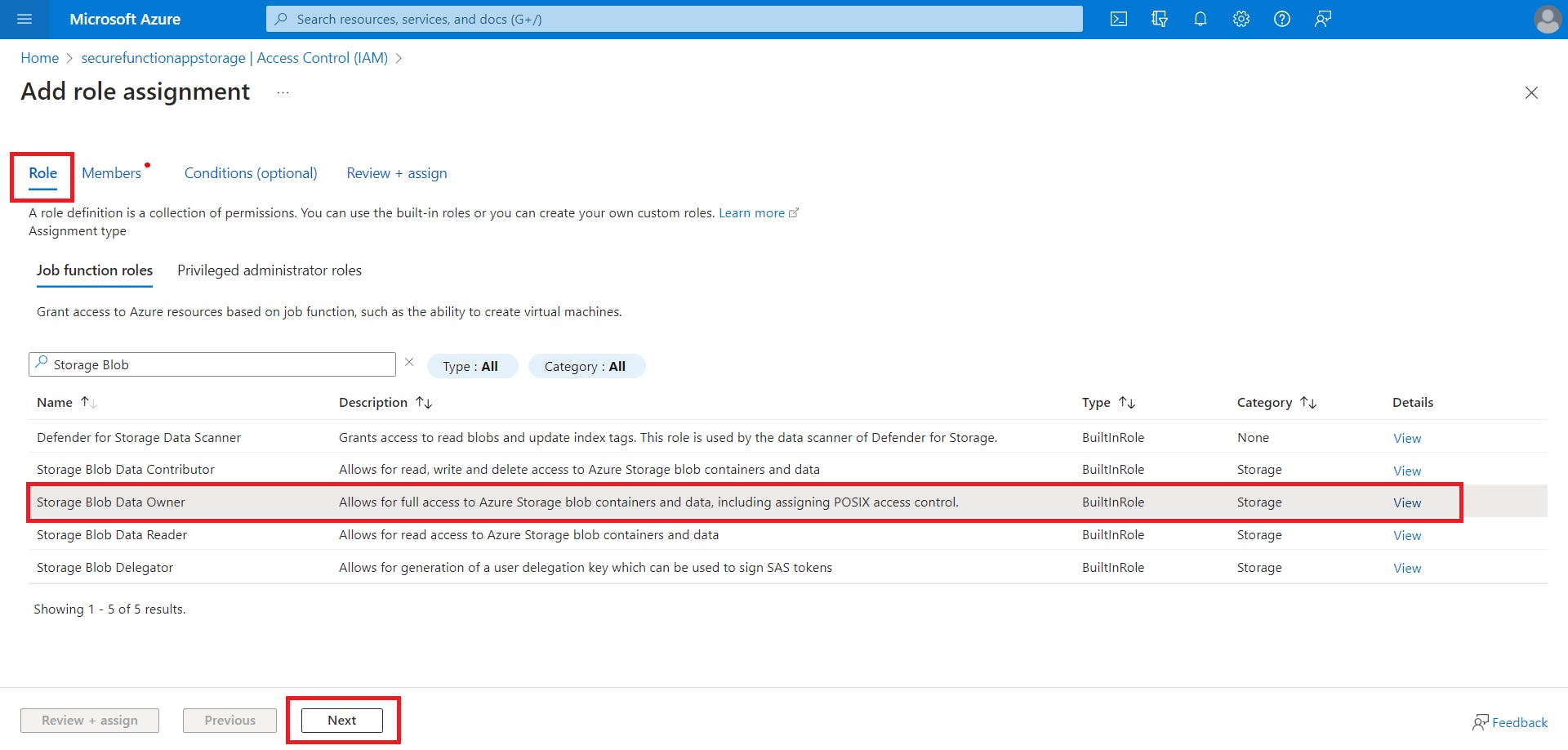
On the Members tab, under Assign access to, select Managed Identity.
Click Select members to open the identities side panel.
Choose the right Subscription, and in the managed identity selector, choose Function App from the System-assigned managed identity category.
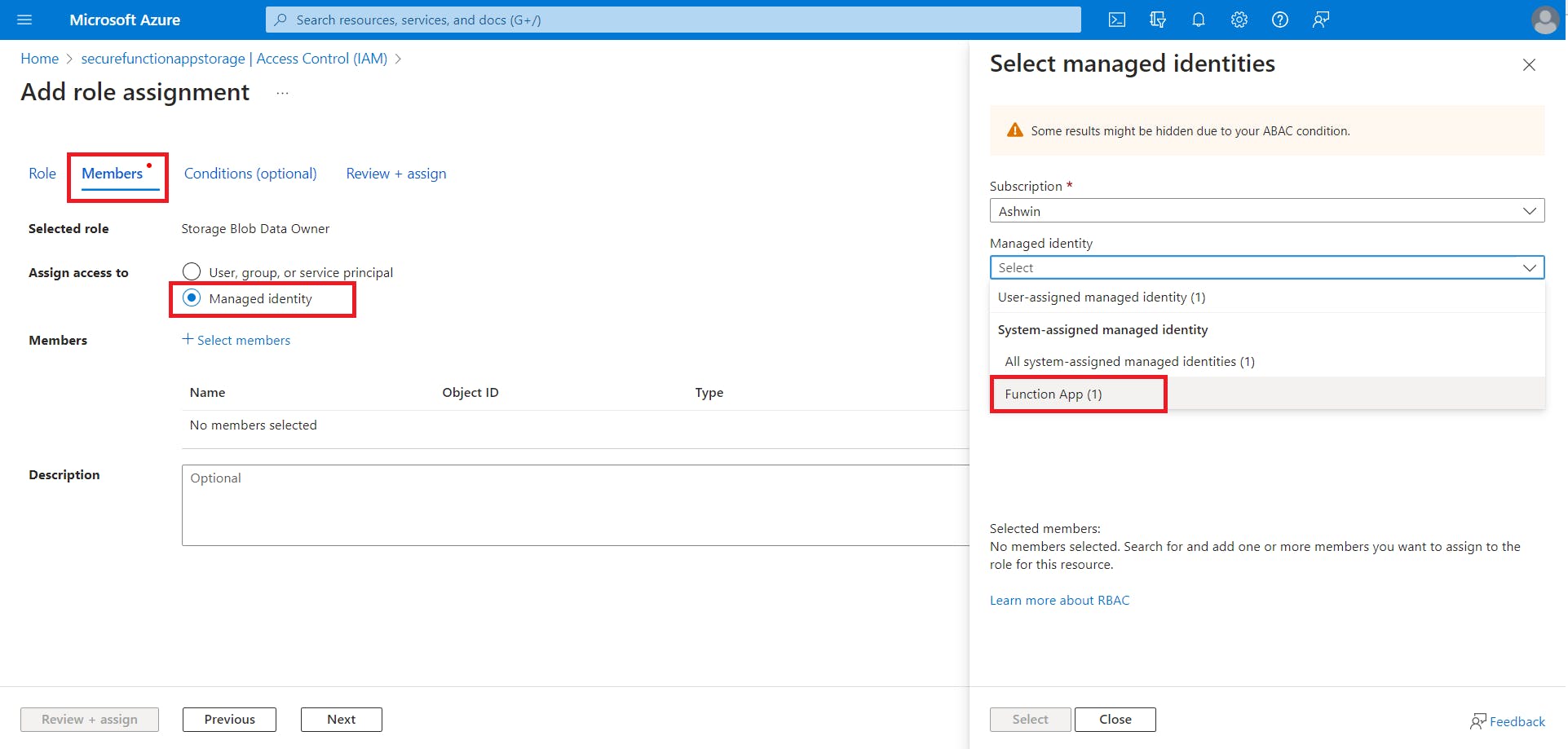
The function app should appear in a list below the input fields. Click on the function app name, and it should now be part of the selected members section. Click Select.

Back on the Add Role Assignment page, click Review + assign. Review the changes, and then click Review + assign.

Edit the 'AzureWebJobsStorage' configuration
Next, update your function app to use the system-assigned identity when connecting to the blob service.
Navigate to your function app, and under Settings, select Configuration.
Select the Edit button next to the AzureWebJobsStorage application setting.
Under Name, change the text from 'AzureWebJobsStorage' to 'AzureWebJobsStorage__accountName' This modified setting instructs the host to use the identity instead of looking for a stored secret. Please note that the new setting uses
__(double underscore), which is a special character in application settings.Under Value, input your storage account name, i.e., replace the connection string with just the storage account name.

Select OK, and then click on Save > Continue to save your changes.
You have now successfully configured the Azure function to connect to the storage account using managed identity instead of the storage connection string containing credentials.
Final thoughts
In this article, we have looked at the essential steps to fortify the security of your Azure Functions when connecting to the host storage account. By embracing the best practice of utilizing Azure Managed Identity (MSI), we mitigate security risks associated with managing account keys and elevate the overall protection of our applications.
This article used the system-assigned managed identity of the function app to connect to the storage account, but even a user-assigned managed identity can be used while granting necessary access to the function & storage account. The use of Managed Identity streamlines the authentication process, eliminating the need for explicit credentials in your code or configurations.
Take charge of your application's security journey, and let Managed Identity be your trusted companion in the realm of Azure services.
Happy coding and stay secure!

